10-01-2023
Authentication Bypass in VMWare Workspace ONE Assist

During a security assessment REQON has discovered multiple security vulnerabilities in the VMWare Workspace ONE Assist software. These vulnerabilities are rated using the CVSSv3.1 risk calculator and vary from critical to medium level risks.
VMware Workspace ONE Assist is a remote support and troubleshooting software that enables IT support teams to remotely access and control end-user devices, including desktops, laptops, and mobile devices. With Workspace ONE Assist, IT support technicians can troubleshoot and resolve issues by remotely accessing and controlling end-user devices, without requiring them to be physically present at the device’s location. The software provides secure remote control capabilities, screen sharing, file transfer, and chat functions.
The software is often also referred to as Remote Assist.
During a security assessment REQON has discovered multiple security vulnerabilities in the software. These vulnerabilities are rated using the CVSSv3.1 risk calculator and vary from critical to medium level risks.
The vulnerabilities have been assigned the following CVE tracking numbers:
- CVE-2022-31685
- CVE-2022-31686
- CVE-2022-31687
- CVE-2022-31688
- CVE-2022-31689
After being notified of the vulnerabilities, VMWare has released multiple security updates to mitigate the discovered findings.
This blog post will provide the Proof of Concept (PoC) code of one of the critically discovered vulnerabilities, namely: Authentication Bypass Vulnerability (CVE-2022-31685).
The PoC of the remaining vulnerabilities is provided in a separate blog post.
Vulnerability description
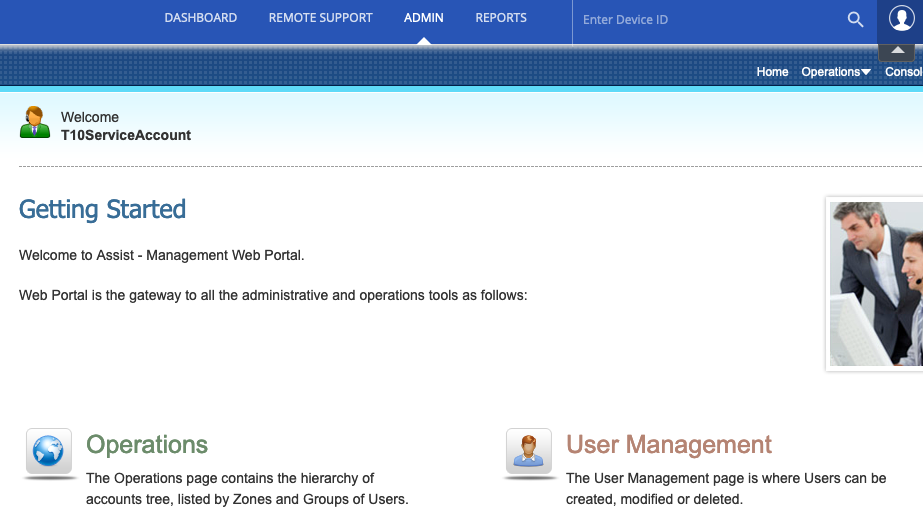
The VMWare ONE Remote Assist application requires an authentication (AUTH) token to perform authorized actions, such as taking over devices, creating and/or changing application users. It was discovered that every installation of the Remote Assist software has an identical valid AUTH-token in the database for the T10ServiceAccount user’s account. This user has ‘superadmin’ permissions within the VMWare ONE remote assist application. The AUTH-token is static for all installations, never expires and never changes after installation.
Impact
This vulnerability allows attackers to authenticate as the T10ServiceAccount (superadmin) on any accessible VMWare ONE remote assist environment. This is also possible if a customer has changed the default password of the T10ServiceAccount user. This essentially makes this vulnerability a full backdoor for all attackers that have knowledge of this vulnerability.
Proof of Concept
Query the database for the AUTH-token of the user with userID 2 and use the given AUTH-token to authenticatie to the vulnerable VMWare ONE Remote Assist instance. The screenshot below show the blurred version of the hardcoded session token.
Remediation
While manually altering or removing the value of the AUTH-token in the database does mitigate the risk of this vulnerability, it does break multiple functionalities of the platform. This is therefore not recommended. Administrators are advised to install the provided patch by VMWare.
To monitor if this vulnerability has been abused in your environment, the application’s logs of the software can be checked for any application calls using this AUTH-token that originate from untrusted IP-addresses.
Note for Pentesters & Red Teamers
VMWare explicitly requested that we did not disclose the precise value of the session token. Therefore, if you intend to demonstrate the proof-of-concept (PoC) or exploit this vulnerability on a vulnerable instance, you must first acquire access to the database of a vulnerable version and extract the token from there. Once you have obtained the token, you will need to analyze the exact flow of HTTP request commands to successfully take control of a device.
Any questions regarding this blog?
Please contact REQON via info@reqon.nl